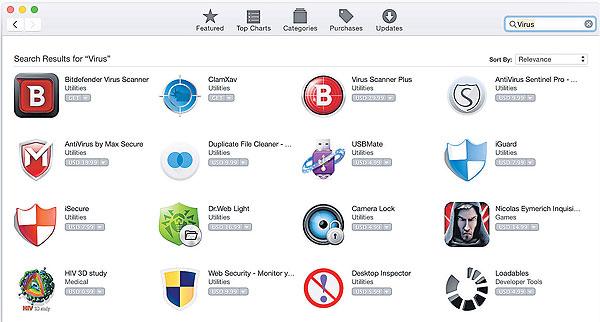
Malware applications in Apple's Mac App Store.
One man's attempt to finally explain whether Apple Macs ever fall victim to 'PC syndrome'
Once in a while, when you are using a Mac online, you may see a warning that your computer has a virus. This is a lie. There are no viruses for OS X. There are other forms of malware, but the self-replicating application that tries to install and embed itself into other programs is not one.
Some sites have headlines that suggest the long-time safety of Macs (itself a myth) has come to an end with the appearance of a virus. Still, there is not one virus that affects OS X, which compares rather favourably with other platforms. Again, let me add that there are forms of malware, including (perhaps most common) the Trojan Horse, worms (few) as well as keyloggers and other spyware.
I was taken to task about this some months ago when I saw a headline on Mac360 in an item on malware by Jack D. Miller, who wrote: "Macs do get viruses, but not many." I asked if the writer could name one, and an attack dog suggested a number of sites that would help me "do my homework". Not one of those links gave me the name of any virus, although there were other forms of malware. Jack D. Miller has not deigned to reply to my comment thus far.
Others, like Kaspersky, for example, who have a vested interest in selling fear, uses the term virus in bait articles. Despite that organisation's apparent credentials, it is only able to list Trojan Horse malware, erroneously calling these "Mac Trojan viruses".
Other sites, including The New York Times have had headlines about Mac viruses, but when analysed by those who know what they are working with, these are found to be examples of Trojan Horse malware. In April 2012, Nicole Perloth was writing about malware, yet used the word "virus". The article included links to sites which had earlier identified the malware (Flashback) in March 2012 and provided methods of cleaning. Apple belatedly also updated its protection to deal with this threat.
As an indication of how limited the problem is, Graham Cluley has 10 years of Mac OS X malware — on a single page. The list includes worms and Trojan Horses. But no virus.
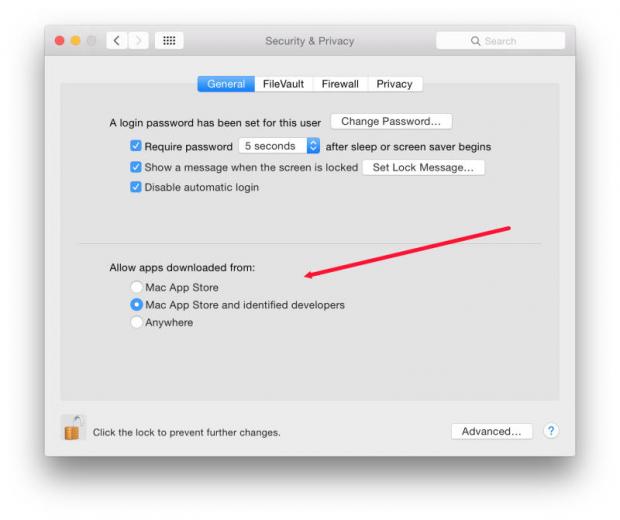
System Preferences, Security & Privacy, showing sandboxing choices.
We should also not forget the Sony rootkit, copy protection measures on CDs from Sony. The main reason that this was installed on so few Macs compared to thousands of PCs was the basic protection that all Macs have: software needs root access to install, and OS X has no root password by design. Macs get round that by a sort of proxy system that uses Admin passwords; but this cannot be done without a user's assistance.
That is why relatively few examples of Trojan Horse malware have been successful. By definition, this needs the user to open a file, such as an image, and that begins the installation. I have seen a few of these: some were sent by email, one via Facebook. Other such false flags have included users trying to access online video and being warned that the performance would be enhanced by downloading a new video codec. Many have, of course.
No one should be complacent. The next major attack may already be here. The weakness of signature checkers, which is the way most virus protection software works on all platforms, is that someone has to find it first. Once it is identified, we can all download the protection, but this is not until the threat is already live and some users have been affected. It's not always good to be first.
There are ways to protect our computers apart from protection software. If we live in a locked room with no internet access, never install any software from outside, never attach external media, and never accept files from others, that should just about do it.
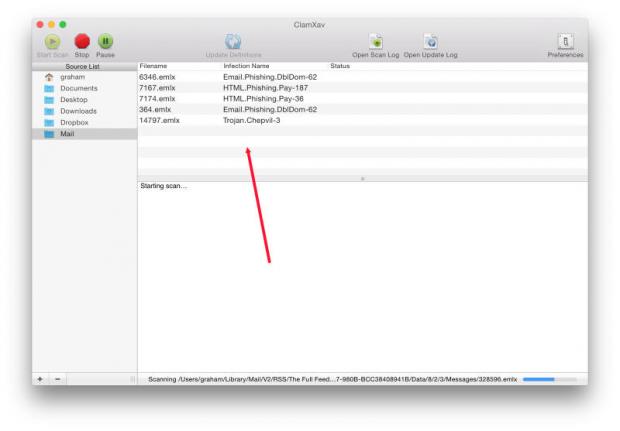
ClamXav checks emails for malware attachments.
That type of clean environment is impractical, so there are ways we can enhance protection, with malware-checkers like ClamXav which I might run once every couple of months. Apple's own sandboxing can be turned on in Security & Privacy preferences, allowing users to select from applications only downloaded from the Mac App Store, from the Mac App Store and identified developers, or Anywhere.
I select the middle road here as some of the developers of useful Mac software have not joined Apple's protection scheme. However, I am unlikely to download software unless I know who the developer is. When such applications are first run, OS X warns the user that they were downloaded.
Some applications are blocked and must be authorised by highlighting the app in the Finder. Control click on the icon and select Open. For those who work in a user account, this needs Admin privileges. Once the password is entered, the app will open and the user will be able to open it in the future.
Graham K. Rogers of Mahidol University's Engineering Faculty has OS X-flavoured web pages at www.extensions.in.th/index4.html
comments powered by Disqus